
Back إدارة مخاطر تقانة المعلومات Arabic مدیریت ریسک در فناوری اطلاعات Persian Gestão de riscos em TI Portuguese Управління ризиками при розробці ПЗ Ukrainian
This article may be too technical for most readers to understand. (November 2013) |
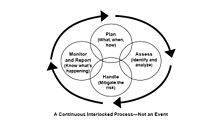
IT risk management is the application of risk management methods to information technology in order to manage IT risk, i.e.:
- The business risk associated with the use, ownership, operation, involvement, influence and adoption of IT within an enterprise or organization
An IT risk management system (ITRMS) can be considered a subcomponent of a wider enterprise risk management system.[1] ITRMS also tend to be integrated into a broader information security management system (ISMS). The establishment, maintenance and continuous update of an ISMS provide a strong indication that a company is using a systematic approach for the identification, assessment and management of information security risks.[2]
Different methodologies have been proposed to manage IT risks, each of them divided into processes and steps.[3]
According to the Risk IT framework,[1] this encompasses not only the negative impact of operations and service delivery which can bring destruction or reduction of the value of the organization, but also the benefit enabling risk associated to missing opportunities to use technology to enable or enhance business or the IT project management for aspects like overspending or late delivery with adverse business impact.[clarification needed incomprehensible sentence]
Because risk is strictly tied to uncertainty, decision theory should be applied to manage risk as a science, i.e. rationally making choices under uncertainty.
Generally speaking, risk is the product of likelihood times impact (Risk = Likelihood * Impact).[4]
The measure of an IT risk can determined as a product of threat, vulnerability and asset values:[5]
A more current risk management framework for IT Risk would be the TIK framework:
The process of risk management is an ongoing iterative process. It must be repeated indefinitely. The business environment is constantly changing and new threats and vulnerabilities emerge every day. The choice of countermeasures (controls) used to manage risks must strike a balance between productivity, cost, effectiveness of the countermeasure, and the value of the informational asset being protected.
- ^ a b "ISACA THE RISK IT FRAMEWORK (registration required)" (PDF). Archived from the original (PDF) on 2010-07-05. Retrieved 2010-12-14.
- ^ Enisa Risk management, Risk assessment inventory, page 46
- ^ Katsicas, Sokratis K. (2009). "35". In Vacca, John (ed.). Computer and Information Security Handbook. Morgan Kaufmann Publications. Elsevier Inc. p. 605. ISBN 978-0-12-374354-1.
- ^ "Risk is a combination of the likelihood of an occurrence of a hazardous event or exposure(s) and the severity of injury or ill health that can be caused by the event or exposure(s)" (OHSAS 18001:2007).
- ^ Caballero, Albert (2009). "14". In Vacca, John (ed.). Computer and Information Security Handbook. Morgan Kaufmann Publications. Elsevier Inc. p. 232. ISBN 978-0-12-374354-1.
© MMXXIII Rich X Search. We shall prevail. All rights reserved. Rich X Search

